The External Secrets Enterprise Edition is product suite is a premium product.
It requires a specific subscription. Contact us for more information.
Overview of the Flow
The process ensures that only legitimate clients can request secrets, and they can only access resources they have been explicitly granted permission for.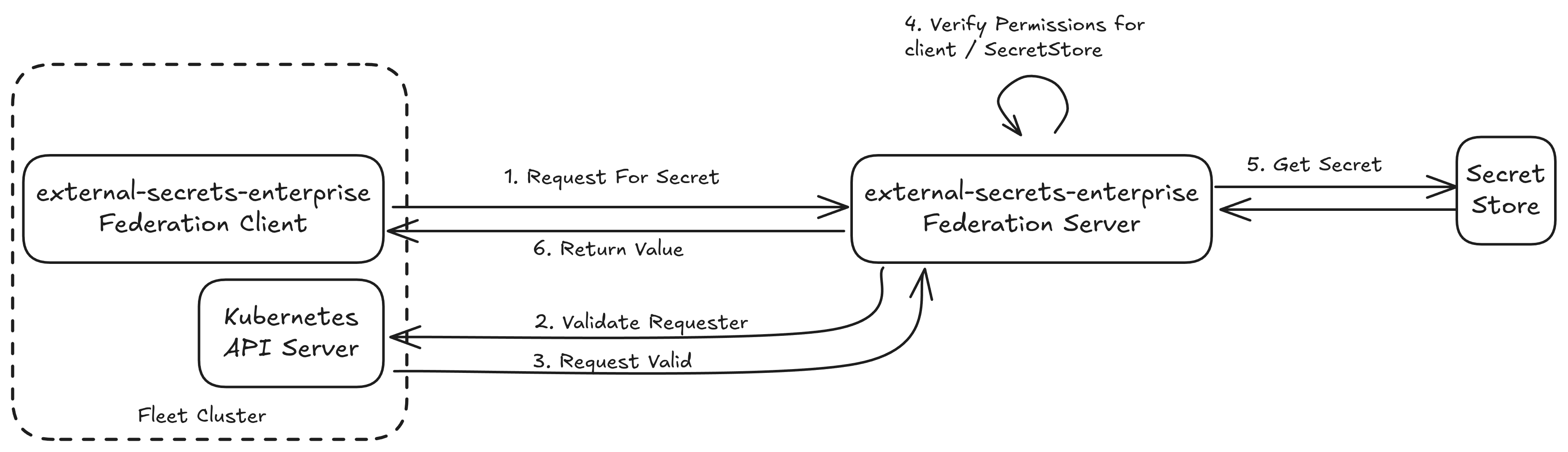
Step-by-Step Breakdown
-
Client Initiates Request & Authentication (Client-Side):
- The Federation Client (e.g.,
esi-clior another ESE instance) prepares to request a secret from the Federation Server. - It retrieves its own Kubernetes Service Account (SA) token. This token is a JSON Web Token (JWT) signed by the client’s Kubernetes cluster.
- It also retrieves its cluster’s CA certificate (the one that signed the keys for its token issuer’s JWKS endpoint).
- The client sends an HTTP request to the appropriate Federation Server API endpoint (e.g.,
/secretstore/...or/generators/...). - Authentication Data Sent:
- The SA token is included in the
Authorization: Bearer <token>HTTP header. - The client cluster’s CA certificate (base64 encoded) is typically sent in the request body, often as part of a JSON payload like
{"ca.crt": "<base64_encoded_ca_cert>"}.
- The SA token is included in the
- The Federation Client (e.g.,
-
Server Receives Request & Validates Token (Server-Side):
- The Federation Server receives the request.
- JWKS URI Construction: It extracts the
issuerclaim from the received JWT. Using this issuer URL and the provided clientca.crt, the Federation Server constructs the JWKS (JSON Web Key Set) URI for the client cluster. Theca.crtis crucial for the Federation Server to trust the client cluster’s OIDC discovery endpoint (where the JWKS is published). - JWKS Fetch & Signature Validation: The Federation Server securely fetches the public keys (JWKS) from the client cluster’s issuer. It then uses these public keys to validate the signature of the SA token. If the signature is invalid, the request is rejected (Authentication Failed).
-
Server Performs Authorization (Server-Side):
- If the token’s signature is valid (Authentication Succeeded), the Federation Server proceeds to authorization.
- It extracts the
issuer(e.g.,https://kubernetes.default.svc.cluster.localof the client) andsubject(e.g.,system:serviceaccount:client-namespace:client-sa-name) claims from the validated token. - Matching
AuthorizationCR: The server searches forAuthorizationCustom Resources defined on its own cluster.- It looks for an
AuthorizationCR wherespec.subject.issuerandspec.subject.subjectexactly match the claims from the client’s token.
- It looks for an
- Verifying
KubernetesFederationLink: It checks that the matchedAuthorizationCR’sspec.federationRef.namepoints to a validKubernetesFederationCR. Theurlin thisKubernetesFederationCR should correspond to the client cluster whose JWKS URI was used for token validation. This ensures the authorization rule is indeed for the authenticated cluster. - Checking Permissions: If a matching and valid
AuthorizationCR is found, the server checks if the resource requested by the client (e.g., a specificClusterSecretStorename or aGeneratorname/kind/namespace) is listed in theallowedClusterSecretStoresorallowedGeneratorssections of thatAuthorizationCR. - If no matching
AuthorizationCR is found, or if the requested resource is not permitted, the request is rejected (Authorization Failed).
-
Secret Retrieval & Response (Server-Side):
- If both authentication and authorization are successful, the Federation Server proceeds to fulfill the request.
- It uses its internal External Secrets Operator mechanisms to fetch the secret data from the permitted
ClusterSecretStoreor to execute the permittedGenerator(using its own credentials to access backend systems like Vault, GCP SM, etc.). - The retrieved or generated secret data is then packaged into an HTTP response and sent back to the Federation Client.
-
Client Receives Secret (Client-Side):
- The Federation Client receives the secret data and processes it (e.g.,
esi-cliinjects it into the environment or files).
- The Federation Client receives the secret data and processes it (e.g.,
This multi-step process, involving cryptographic validation of tokens and explicit policy checks via CRDs, ensures that secret data is only shared between trusted and explicitly authorized entities.
