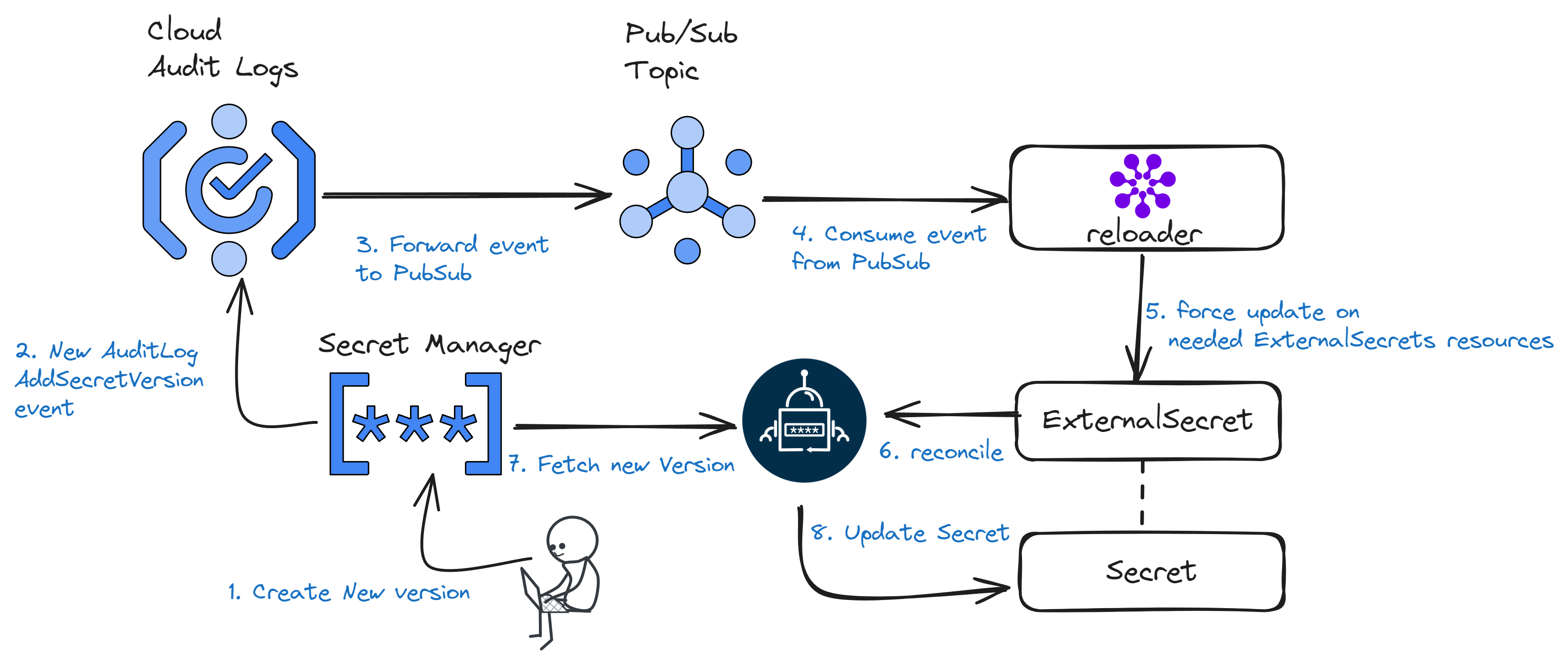
How it Works
reloader will listen for audit log events from a given GCP PubSub, and, based on pattern matching,
will trigger an ExternalSecret reconciliation if that object queries the GCP Secret Manager key that had its version updated.
The diagram below gives an overview of the setup:
Setting Up GCP
In order to set up GCP, four steps are needed:- Create a Topic and a Subscription on GCP Pub/Sub
- Create a Log Router to send information from Audit Logs to PubSub
- Create a Service Account & Permissions for
reloader - Install
reloaderin your cluster
The following terraform code
contains a recipe for everything needed within GCP using service account keys.
We recommend using it with a local
kind cluster for a quick onboarding experience - use workload identity in production environments.reloader within your cluster.
[Optional] Enable Service APIs
[Optional] Enable Service APIs
Create a Topic and a Subscription on GCP Pubsub
Create a Topic and a Subscription on GCP Pubsub
Create a Log router for the PubSub Topic
Create a Log router for the PubSub Topic
Create Service Account & Permissions (Service Account Keys)
Create Service Account & Permissions (Service Account Keys)
Create Service Account & Permissions (Workload Identity)
Create Service Account & Permissions (Workload Identity)
reloader
Example Configuration
Before applying this manifest, be sure to have installed
reloader first.AddSecretVersion message will automatically update your Kubernetes Secret values!