The External Secrets Inc. Audit & Compliance product suite is a premium product.
It requires a specific subscription. Contact us for more information.
Understanding Policy Execution Types
Policies can be executed at different times during the secret lifecycle. The execution type of a policy determines when the policy is evaluated and when the policy is enforced.
Almost all policy types are evaluated as soon as a new event arrives from the Provider Audit Logs.
The exception is the Results policy type, which is evaluated after the secret is updated and the results of the update are available.
Every event message has a OriginalPayload field that contains the original event message sent from the provider.
From this message, it is possible to create policy logic that depends on specific provider information (such as audit log dates, authorization fields, or generic policy parsing).
Check Provider Session to get more information on each OriginalPayload format.
Policy Execution Types
The following are the available policy execution types:
Create
Policies with this execution type are evaluated when a secret is created.
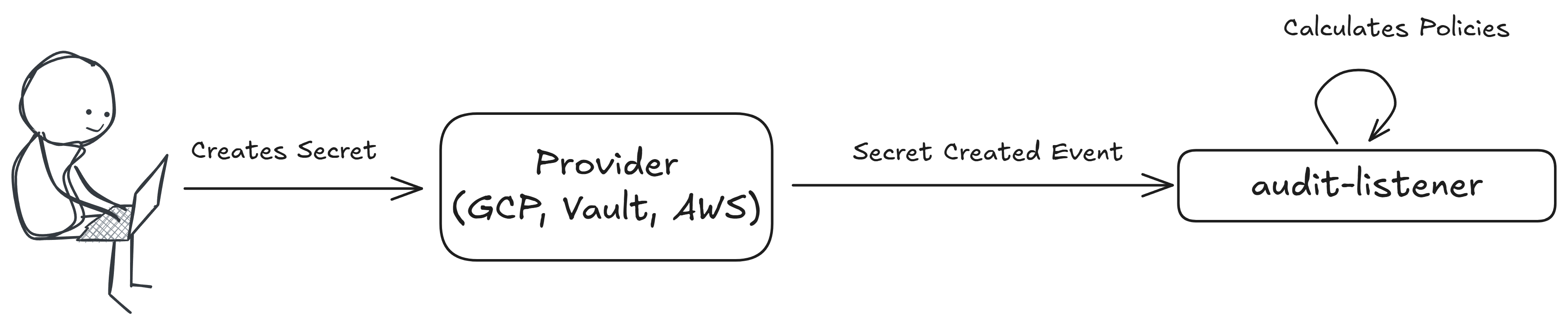
 This policy is executed on the following event message:
This policy is executed on the following event message:
{
"SecretName": "string",
"ProviderId": "<uuid>",
"ActorIdentifier": "string",
"Timestamp": "2024-12-29T00:00Z",
"OriginalPayload": {},
"ProviderSecretId": "string"
}
Update
Policies with this execution type are evaluated when a secret is updated.
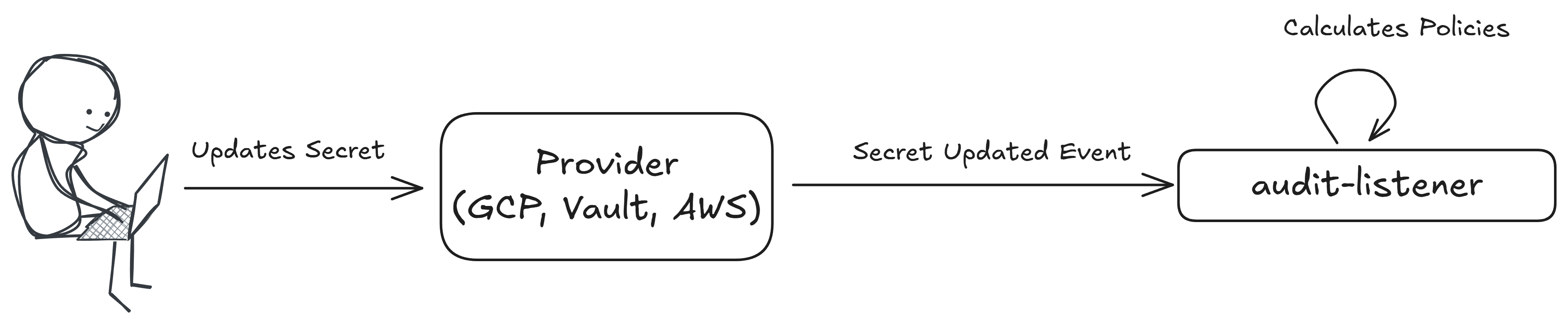
 This policy is executed on the following event message:
This policy is executed on the following event message:
{
"SecretName": "string",
"ProviderId": "<uuid>",
"ActorIdentifier": "string",
"Timestamp": "2024-12-29T00:00Z",
"Data": {},
"OriginalPayload": {},
"ProviderSecretId": "string"
}
Read
Policies with this execution type are evaluated when a secret is read.
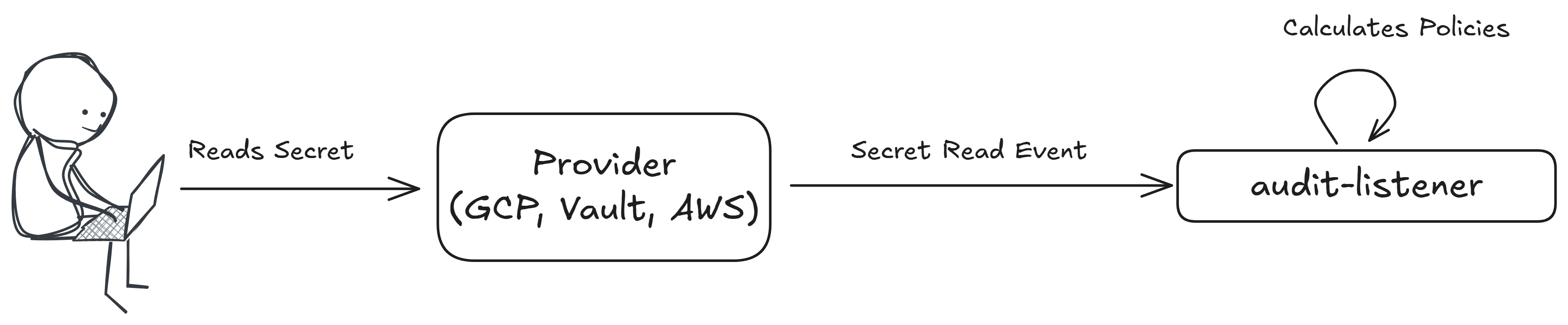
 This policy is executed on the following event message:
This policy is executed on the following event message:
{
"SecretName": "string",
"ProviderId": "<uuid>",
"ActorIdentifier": "string",
"Timestamp": "2024-12-29T00:00Z",
"OriginalPayload": {}
}
Delete
Policies with this execution type are evaluated when a secret is deleted.
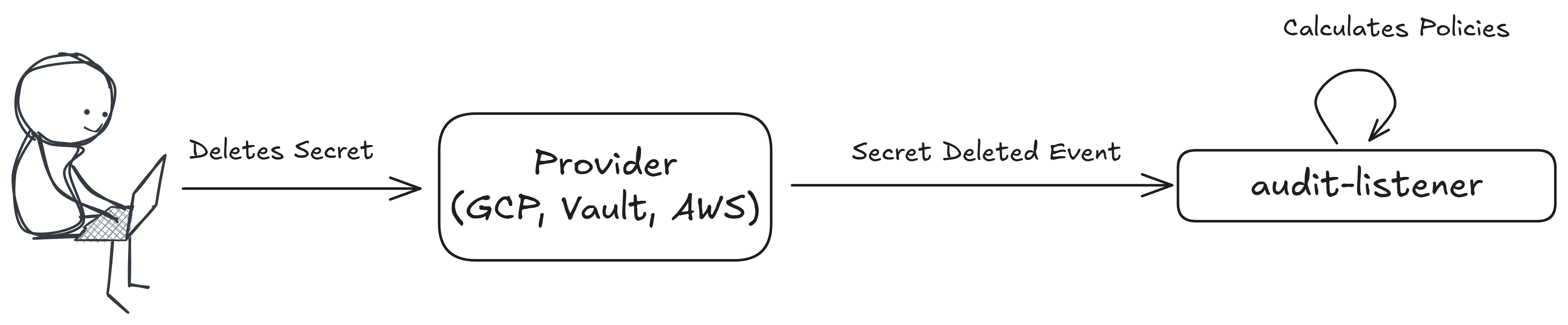
 This policy is executed on the following event message:
This policy is executed on the following event message:
{
"SecretName": "string",
"ProviderId": "<uuid>",
"ActorIdentifier": "string",
"Timestamp": "2024-12-29T00:00Z",
"OriginalPayload": {}
}
RBACCreate
Policies with this execution type are evaluated when a secret RBAC is created.
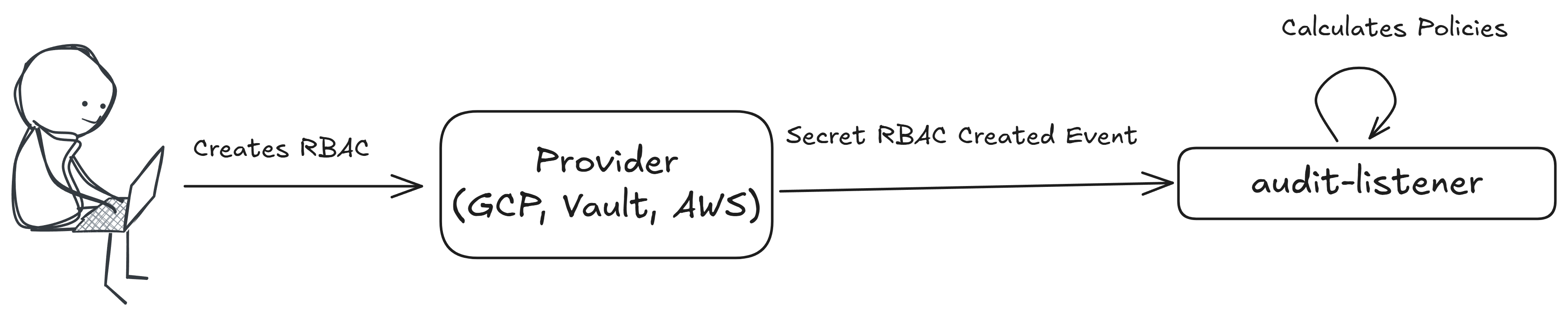
 This policy is executed on the following event message:
This policy is executed on the following event message:
{
"SecretName": "string",
"RbacId": "<uuid>",
"ProviderId": "<uuid>",
"Timestamp": "2024-12-29T00:00Z",
"Data": {
"permission": "string",
"principal": "string",
"scope": "string"
},
"OriginalPayload": {},
"ActorIdentifier": "string"
}
RBACUpdate
Policies with this execution type are evaluated when a secret RBAC is updated.
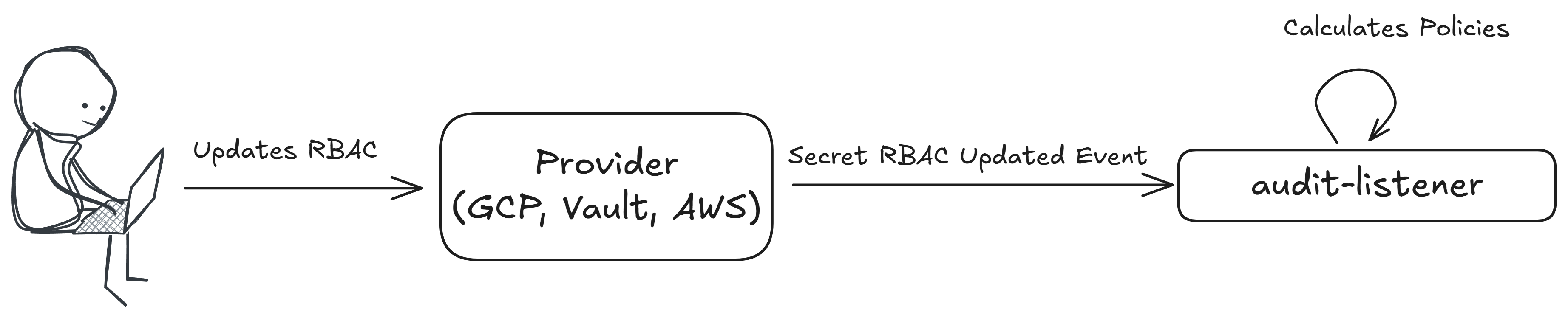
 This policy is executed on the following event message:
This policy is executed on the following event message:
{
"SecretName": "stringt",
"RbacId": "<uuid>",
"ProviderId": "<uuid>",
"Timestamp": "2024-12-29T00:00Z",
"from": {
"permission": "string",
"principal": "string",
"scope": "string"
},
"to": {
"permission": "string",
"principal": "string",
"scope": "string"
},
"OriginalPayload": {},
"ActorIdentifier": "string"
}
RBACDelete
Policies with this execution type are evaluated when a secret RBAC is deleted.
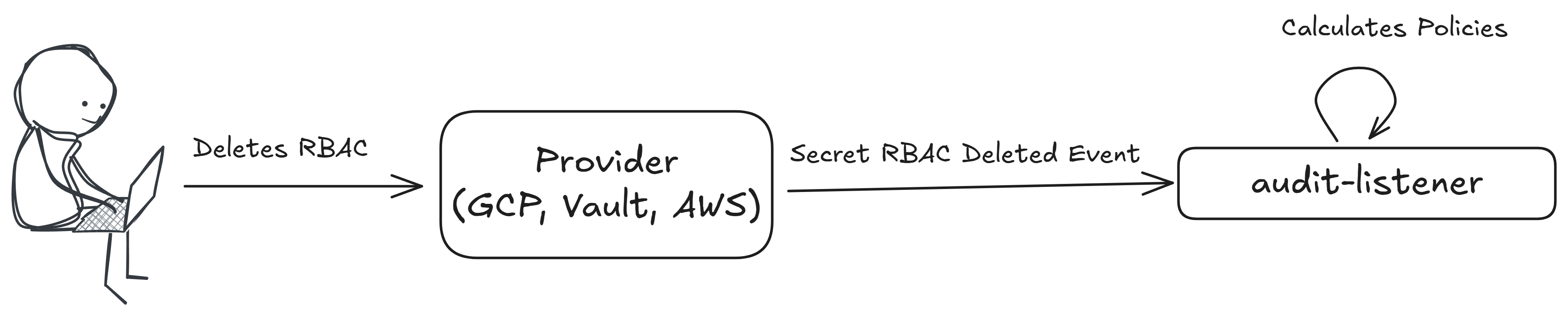
 This policy is executed on the following event message:
This policy is executed on the following event message:
{
"SecretName": "string",
"RbacId": "<uuid>",
"ProviderId": "<uuid>",
"Timestamp": "2024-12-29T00:00Z",
"Data": {
"permission": "string",
"principal": "string",
"scope": "string"
},
"OriginalPayload": {},
"ActorIdentifier": "string"
}
Results
Policies with this execution type are evaluated when a secret is updated and the results of the update are available.

 This policy is executed on the following event message:
This policy is executed on the following event message:
{
"SecretName": "string",
"LastRotation": "2024-12-29T00:00:00Z",
"LastAccess": "2024-12-29T00:00:00Z",
"ProviderId": "<uuid>",
"Duplicates": [
{
"Id": "string",
"Provider": "<uuid>"
}
],
"Accessors": [
{
"Id": "<uuid>",
"Name": "string",
"AccessTime": "2024-12-29T00:00:00Z"
}
],
"Timestamp": "2024-12-29T00:00:00Z"
}















