The External Secrets Inc. Audit & Compliance product suite is a premium product.
It requires a specific subscription. Contact us for more information.
AWS Parameter Store Provider
The Audit Listener can be configured to receive audit logs from AWS Parameter Store by utilizing a SQS queue, Event Bridge and a Cloud Trail. The illustration below demonstrates the setup: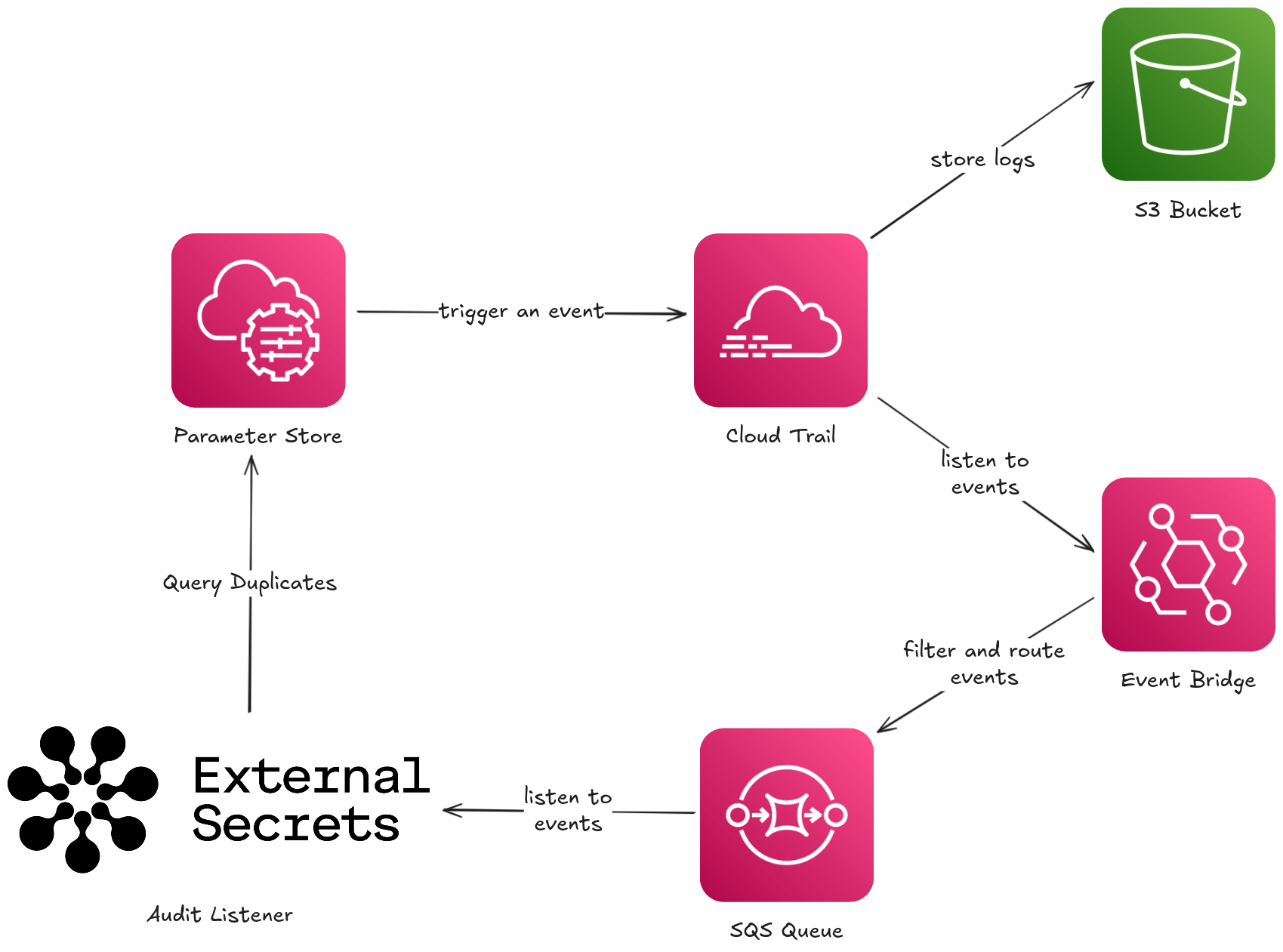
Required Permissions
To setup the Listener, the following permission must be assigned:sqs:ReceiveMessagesqs:DeleteMessagessm:GetParametersByPathssm:GetParameterkms:Decrypt
The GetParameter, GetParametersByPath and Decrypt permissions are necessary for the listener to calculate duplicate entries.
Policy Example
Configuring the Provider
Setting up the provider may require configuration of the authentication methods during the listener installation process.Supported Authentication Methods
The Audit Listener supports the following AWS authentication methods:- Using a Access Key and Secret Access Key defined in the runtime.
- Using an IAM role for tasks when using ECS task definition or the RunTask API operation.
- Using an IAM role for Amazon EC2 when your is running on an EC2 instance.
- Using IAM Role for Service Account when running on EKS.
Access Key and Secret Access Key
Access Key and Secret Access Key
Setup with Kustomize
Setup with Kustomize
Create a patch file named
aws-patch.yaml with the following content:Setup with Helm
Setup with Helm
Add the following values to the helm install:
Setup on Standalone VMs
Setup on Standalone VMs
Execute the following command using an account with appropriate privileges:
systemd edit audit-listener.serviceThen, edit the file to include the necessary environment variables:ECS Task Definition or RunTask API
ECS Task Definition or RunTask API
Setup with Kustomize
Setup with Kustomize
- This method is incompatible with Kubernetes installations.
Setup with Helm
Setup with Helm
- This method is incompatible with Kubernetes installations.
Setup on Standalone VMs
Setup on Standalone VMs
- No additional setup is required for authentication when using ECS task definition or the RunTask API operation
Running on an EC2 instance
Running on an EC2 instance
Setup with Kustomize
Setup with Kustomize
Add the following
aws-sa-patch.yaml to the kustomization file:Setup with Helm
Setup with Helm
Add the following values to the helm install:
Setup on Standalone VMs
Setup on Standalone VMs
- This authentication method is not supported for standalone installations.
IAM Role for Service Account on EKS
IAM Role for Service Account on EKS
Setup with Kustomize
Setup with Kustomize
Create a patch file named
aws-sa-patch.yaml with the following content:Setup with Helm
Setup with Helm
Add the following values to the helm install:
Setup on Standalone VMs
Setup on Standalone VMs
- This authentication method is not supported for standalone installations.
Creating a new Provider
After completing the listener setup, you can create a new provider.- Navigate to the Dashboard.
- Add a new provider:
- Select
AWS_PARAMETER_STOREas the provider type. - Specify the fields based on your installation:
Region: AWS region.QueueURL: SQS queue endpoint URL.
- Select
Setting Up AWS
- Create S3 Bucket that will be used to store Cloud Trail logs
- Create a Trail on Cloud Trail
- Create SQS queue that will be consumed by Audit Listener
- Configure Event Bridge to route Parameter Store events to SQS
